Global Privileged Identity Management Market, By Component (Solution, Services), Installation Type (Agent-based, Appliance-based), Deployment Mode, Organization Size, Industry Vertical, and Region – Industry Analysis and Forecast to 2030
The global privileged identity management market is expected to grow from USD 2.87 billion in 2023 to USD 7.97 billion by 2030 at a CAGR of 15.7%. The market is driven by factors such as the growing recognition of the risks associated with privileged accounts, regulatory requirements, insider threats, cloud adoption, data privacy concerns, and the need for operational efficiency. The market continues to grow as organizations seek comprehensive solutions to secure and manage their privileged accounts effectively.
Figure 1: Global Privileged Identity Management Market Size, 2023-2030 (USD Billion)
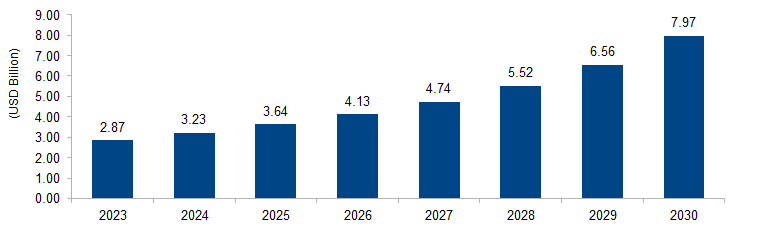
Source: Secondary Research, Expert Interviews, and MAARECO Analysis
Privileged Identity Management (PIM) is a comprehensive approach to managing and securing privileged accounts within an organization. Privileged accounts have elevated access rights and permissions, granting users the ability to control critical systems, sensitive data, and perform administrative tasks. PIM focuses on ensuring the confidentiality, integrity, and availability of privileged accounts by implementing processes, policies, and technologies.
PIM solutions encompass a range of capabilities, including privileged account discovery, password management, access control, session monitoring, and privileged user activity auditing. These solutions aim to centralize and streamline the management of privileged accounts, enforcing strong authentication, least privilege principles, and accountability measures.
By implementing PIM, organizations can minimize the risk of unauthorized access, prevent potential security breaches, and enhance the overall security posture. PIM helps organizations adhere to regulatory compliance requirements, detect and mitigate insider threats, secure privileged access in cloud environments, and maintain operational efficiency.
Privileged Identity Management is a holistic approach that enables organizations to effectively manage and secure privileged accounts, reducing the risk of compromise and ensuring the proper handling of critical systems and sensitive data.
Privileged Identity Management Market Drivers
Data privacy and confidentiality
Privileged accounts often have access to highly sensitive data, intellectual property, and critical infrastructure within organizations. Protecting the confidentiality and privacy of this data is essential to mitigate the risks of data breaches, unauthorized access, and data leakage.
Privileged Identity Management plays a crucial role in securing privileged accounts and enforcing data protection measures. By implementing strong authentication mechanisms, access controls, and encryption, this solution ensure that only authorized individuals can access privileged accounts and the associated sensitive data. They also enforce the principle of least privilege, granting users only the necessary access privileges to perform their specific tasks, thereby reducing the risk of data exposure.
Additionally, PIM solutions enable organizations to monitor and audit privileged user activities. By capturing and analyzing privileged user sessions, organizations can detect and investigate any suspicious or unauthorized activities. This proactive monitoring helps ensure that privileged accounts are used appropriately and helps identify potential insider threats or external attacks targeting sensitive data.
Data privacy regulations, such as the General Data Protection Regulation (GDPR) and other regional data protection laws, require organizations to implement measures to protect personal data. Privileged Identity Management assists organizations in meeting these regulatory requirements by securing privileged accounts that have access to personal data, enforcing strict access controls, and providing audit trails to demonstrate compliance.
Need for operational efficiency and productivity
The need for operational efficiency and productivity is a significant driver for the Privileged Identity Management (PIM) market. Organizations recognize that managing privileged accounts manually can be time-consuming, error-prone, and resource-intensive. PIM solutions address these challenges by streamlining and automating privileged account management processes, resulting in improved operational efficiency and enhanced productivity.
PIM solutions offer features such as automated password management, which eliminates the need for users to remember and update complex passwords for privileged accounts. This automation reduces the burden on IT support teams, increases productivity, and ensures strong password practices are enforced consistently across privileged accounts.
Moreover, PIM solutions provide centralized management capabilities, allowing administrators to handle privileged account provisioning and deprovisioning efficiently. With automated workflows and role-based access controls, administrators can assign appropriate access privileges to users based on their roles and responsibilities. This reduces manual effort, eliminates the risk of overprivileged access, and enhances overall operational efficiency.
PIM solutions also facilitate session monitoring and recording, enabling organizations to monitor privileged user activities in real-time. This capability improves visibility into privileged account usage and helps identify any abnormal or suspicious behavior, aiding in the detection of insider threats or external attacks. By proactively monitoring privileged sessions, organizations can enhance security while ensuring operational continuity.
Efficient and streamlined privileged account management through PIM solutions minimizes downtime associated with account-related issues and reduces the risk of errors or misconfigurations. This results in increased productivity for both IT administrators and privileged users, allowing them to focus on critical tasks rather than being burdened with manual processes. These factors drive the privileged identity management market.
Privileged Identity Management Market Restraints
Resistance to change
Resistance to change is a significant restraint in the Privileged Identity Management (PIM) market. Introducing a PIM solution often requires organizations to modify existing privileged account management processes, workflows, and user access privileges. This can lead to resistance from employees who are accustomed to established practices and may be reluctant to adopt new approaches.
Resistance to change can manifest in various ways. Employees may be hesitant to embrace unfamiliar technologies or processes, fearing that they will disrupt their daily routines or increase their workload. Additionally, there may be concerns about the learning curve associated with using a new PIM solution, especially for employees who are not well-versed in technical concepts. The fear of making mistakes or losing efficiency during the transition can also contribute to resistance.
Overcoming resistance to change requires a comprehensive approach. Clear communication is essential to help employees understand the benefits of PIM and how it aligns with the organization’s security goals. Highlighting the potential risks of not implementing PIM can create awareness and urgency for change. Providing training and support to employees during the transition period is crucial to alleviate concerns and build confidence in the new system.
Engaging key stakeholders and involving them in the decision-making process can help address resistance. By actively seeking input, addressing concerns, and involving employees in the implementation of PIM, organizations can foster a sense of ownership and reduce resistance. Additionally, establishing a change management strategy that includes regular communication, training sessions, and ongoing support can help employees adapt to the new PIM solution more smoothly.
Organizational culture plays a significant role in overcoming resistance to change. Creating a culture that values security and emphasizes the importance of privileged account management can facilitate acceptance of PIM. Leadership support and reinforcement of the need for Privileged Identity Management as a standard practice can help employees recognize its value and alleviate concerns about change.
Cost considerations
Implementing a comprehensive PIM solution involves various costs that organizations need to evaluate and justify. These costs include software licenses, infrastructure upgrades, training, ongoing maintenance, and potential integration expenses.
The initial investment required to procure PIM software licenses and deploy the necessary infrastructure can be substantial. The cost of acquiring and implementing a PIM solution can be a barrier, particularly for small and medium-sized businesses with limited budgets. Organizations must carefully assess the financial feasibility of implementing a PIM solution and weigh it against the potential benefits and risks.
In addition to the upfront costs, ongoing maintenance and support expenses must be considered. PIM solutions require regular updates, patches, and upgrades to keep pace with evolving security threats and maintain compatibility with the organization’s IT infrastructure. Organizations need to allocate resources for dedicated IT staff or engage with third-party providers to ensure the effective maintenance and support of the PIM solution.
Integration costs can also arise when integrating PIM with existing identity and access management systems, directory services, or other security infrastructure. The complexity of integration, customizations, and data migration can contribute to the overall cost of implementing PIM. These factors restrain the privileged identity management market.
To address cost considerations, organizations can explore different options such as cloud-based PIM solutions or managed service offerings. These alternatives can provide cost-effective options by shifting some of the costs to subscription-based models or outsourcing aspects of PIM management to specialized service providers. Conducting a thorough cost-benefit analysis and considering long-term savings from improved security and operational efficiencies is crucial in making informed decisions regarding PIM implementation.
Overall, organizations need to carefully evaluate the costs associated with implementing and managing a PIM solution. Considering budget constraints, return on investment, and the specific security needs of the organization is vital to ensure a well-balanced approach to privileged account management while managing costs effectively.
Privileged Identity Management Market Opportunities
Cloud-based PIM solutions
Cloud-based Privileged Identity Management (PIM) solutions offer significant opportunities in the market due to the increasing adoption of cloud services and the need for centralized, scalable, and flexible privileged access management. Cloud-based PIM solutions leverage the power of cloud computing to provide organizations with enhanced capabilities and benefits.
One key opportunity is the scalability offered by cloud platforms. As organizations expand their operations or experience fluctuating demands, cloud-based PIM solutions can easily scale to accommodate growing numbers of privileged accounts and users. The elastic nature of cloud infrastructure allows organizations to adjust resources dynamically, ensuring efficient management of privileged access without the need for extensive infrastructure investments.
Flexibility is another advantage of cloud-based PIM solutions. With the proliferation of hybrid and multi-cloud environments, organizations can deploy PIM solutions that seamlessly integrate with various cloud platforms and provide consistent management of privileged accounts across different environments. Cloud-based PIM solutions offer centralized administration, policy enforcement, and access controls, allowing organizations to maintain a holistic view of privileged access irrespective of the cloud service provider or deployment model used.
Cost-effectiveness is a significant opportunity provided by cloud-based privileged identity management solutions. Organizations can leverage the pay-as-you-go model of cloud services, eliminating the need for substantial upfront investments in infrastructure. They can avoid costs associated with hardware procurement, maintenance, and scalability, as cloud providers handle these aspects. The cloud-based approach also reduces the burden of managing and upgrading PIM infrastructure, allowing organizations to focus on their core operations while benefiting from the latest PIM features and updates provided by the cloud service provider.
Additionally, cloud-based PIM solutions often offer high availability and disaster recovery capabilities. Cloud platforms provide redundancy and robust backup mechanisms, ensuring continuous access to privileged accounts even in the event of hardware failures or disruptions. This reliability and resilience are crucial for organizations to maintain operational continuity and minimize any potential impact on critical systems and data.
Integration with Identity and Access Management (IAM)
Integration with Identity and Access Management (IAM) presents a significant opportunity in the Privileged Identity Management (PIM) market. IAM focuses on managing user identities, authentication, and access controls across an organization’s IT ecosystem. Integrating PIM with IAM solutions offers several benefits and opportunities for enhanced security and streamlined access management.
One key opportunity is the establishment of a unified and comprehensive approach to identity and access management. By integrating PIM with IAM, organizations can seamlessly manage both privileged and non-privileged user accounts within a single system. This integration allows for consistent access controls, policies, and workflows across all types of user accounts, reducing complexity and ensuring a holistic approach to access management.
The integration also enables organizations to leverage IAM’s features and capabilities to enhance privileged account security. IAM solutions often provide robust authentication mechanisms, such as multi-factor authentication, which can be extended to privileged accounts. This ensures that only authorized individuals can access privileged accounts, reducing the risk of unauthorized access and potential security breaches.
Moreover, integrating privileged identity management with IAM solutions streamlines user provisioning and deprovisioning processes. When a user’s non-privileged account is created or deactivated in the IAM system, the corresponding privileged account can be automatically provisioned or deprovisioned in the PIM system. This automation reduces manual effort, minimizes the risk of errors or oversights, and improves operational efficiency.
Another opportunity is the ability to enforce consistent access policies and segregation of duties (SoD) controls across all user accounts. IAM solutions often provide SoD capabilities to prevent conflicts of interest and enforce separation of duties. By integrating PIM with IAM, organizations can extend these controls to privileged accounts, ensuring that users with privileged access are not granted conflicting roles or permissions that could compromise security. These factors offer new opportunities to the privileged identity management market.
Privileged Identity Management Market Challenges
Privileged account discovery and management
One of the significant challenges in the Privileged Identity Management (PIM) market is privileged account discovery and management. Organizations often struggle with the comprehensive identification and management of all privileged accounts within their IT infrastructure. Privileged accounts can exist across various systems, platforms, databases, and applications, making it difficult to have a complete view of privileged access.
The challenge lies in discovering and cataloging all privileged accounts accurately. It requires organizations to conduct thorough assessments and audits to identify all accounts with elevated privileges, including local accounts, service accounts, and shared accounts. Additionally, organizations must consider dynamic environments where new privileged accounts can be created or existing accounts modified frequently.
Once privileged accounts are discovered, organizations face the challenge of effectively managing them. This includes enforcing strong password policies, regularly rotating passwords, and ensuring that access privileges are granted based on the principle of least privilege. Organizations need to establish proper workflows and controls for privileged account provisioning, deprovisioning, and periodic access reviews.
Moreover, managing privileged accounts involves implementing robust access controls, session monitoring, and audit capabilities to prevent unauthorized access and detect any suspicious activities. Monitoring privileged user activities in real-time is crucial to identify potential security breaches or insider threats.
Compliance and regulatory requirements
Compliance with regulatory requirements is a significant challenge in the Privileged Identity Management (PIM) market. Organizations need to ensure that their privileged account management practices align with various industry-specific regulations, data protection laws, and compliance frameworks. Meeting these requirements poses several challenges.
Firstly, different regulations and frameworks have varying requirements for privileged account management. For instance, the General Data Protection Regulation (GDPR) mandates organizations to implement appropriate technical and organizational measures to protect personal data, including privileged access. Other regulations such as the Payment Card Industry Data Security Standard (PCI DSS) and the Health Insurance Portability and Accountability Act (HIPAA) have specific requirements for controlling privileged access to sensitive financial and healthcare data. Navigating and addressing the unique requirements of multiple compliance frameworks can be complex and time-consuming for organizations.
Secondly, privileged accounts often have broad access to critical systems and sensitive data. Ensuring compliance with regulatory requirements requires organizations to implement strong access controls, enforce segregation of duties (SoD), and maintain audit trails of privileged user activities. Organizations need to demonstrate that they have implemented appropriate controls, monitored privileged access, and conducted regular access reviews.
Furthermore, compliance requirements often evolve over time. New regulations may be introduced, or existing ones may be updated, requiring organizations to adapt their privileged account management practices accordingly. Staying abreast of regulatory changes and proactively implementing necessary updates to meet compliance can be challenging for organizations, particularly those operating in multiple jurisdictions or industries with overlapping regulations.
Another challenge is demonstrating compliance through audits and assessments. Organizations must be able to provide evidence of their adherence to regulatory requirements, including privileged account management controls and monitoring practices. Preparing for and successfully navigating compliance audits require substantial documentation, evidence of control implementation, and clear visibility into privileged account activities. These factors pose challenges to the privileged identity management market.
Regional Trends
North America: North America has been a prominent region in terms of PIM adoption. The United States, in particular, has a mature cybersecurity market and a strong focus on data protection and privacy regulations. Organizations in North America have been early adopters of PIM solutions to enhance privileged account security, comply with regulations such as GDPR and PCI DSS, and mitigate the risks associated with data breaches and insider threats.
Europe: Europe has witnessed significant growth in PIM adoption due to stringent data protection regulations like GDPR. Organizations in countries such as the United Kingdom, Germany, and France have invested in PIM solutions to ensure compliance, protect sensitive data, and mitigate security risks. European enterprises are increasingly recognizing the importance of privileged account security and the role of PIM in safeguarding critical assets.
Asia Pacific: The Asia Pacific region is experiencing a growing focus on PIM. Countries like China, Japan, South Korea, and India are investing in cybersecurity measures, including PIM solutions, to address the rising cyber threats and secure privileged accounts. The region’s rapid digital transformation, increasing regulatory requirements, and a surge in cyberattacks have driven the demand for PIM solutions to protect valuable data assets and ensure compliance.
Latin America: Latin America is gradually recognizing the importance of privileged account security and the need for PIM solutions. Countries like Brazil, Mexico, and Argentina are witnessing an increasing adoption of PIM solutions, driven by factors such as the need to comply with data protection regulations, protect sensitive information, and address insider threats. The region’s expanding digital landscape and growing cybersecurity concerns are fueling the demand for robust PIM solutions.
Middle East and Africa: The Middle East and Africa region is showing growing interest in PIM solutions as organizations in sectors like finance, energy, and government recognize the importance of securing privileged accounts. Countries like the United Arab Emirates, Saudi Arabia, and South Africa are investing in cybersecurity infrastructure and technologies, including PIM, to protect critical systems and sensitive data.
Key Players
Key players operating in the global privileged identity management market are BeyondTrust, Thycotic, One Identity, Simeio Solutions, Centrify, Oracle, Core Security, Quest Software, CyberArk, ObserveIT, IBM, CA Technologies, Broadcom, Micro Focus, Hitachi ID Systems, Zoho Corp, Onion ID, Silverlake MasterSAM, and Osirium.
PRICE
ASK FOR FREE SAMPLE REPORT