Global IoT Security Market, By Component (Solutions, Services), Security Type (Network Security, Endpoint Security, Application Security, Data Security), Deployment Mode (Cloud, On-premises), Application Area, and Region – Industry Analysis and Forecast to 2030
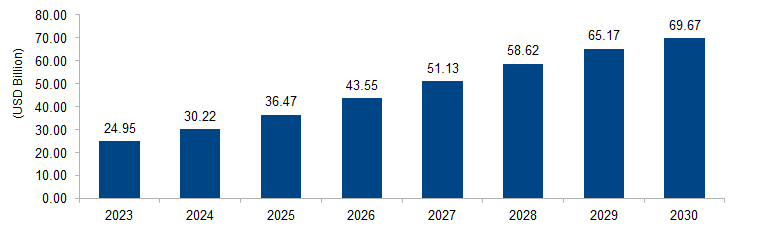
The global IoT Security market is expected to grow from USD 24.95 billion in 2023 to USD 69.67 billion by 2030 at a CAGR of 15.8%. The IoT security market is driven by the exponential growth of interconnected devices, raising concerns about cybersecurity threats. As the Internet of Things (IoT) expands across industries, the need to safeguard sensitive data and protect against potential breaches becomes paramount. The escalating frequency and sophistication of IoT-related cyber attacks fuel the demand for robust security solutions to ensure the integrity and confidentiality of interconnected systems.
Figure 1: Global IoT Security Market Size, 2023-2030 (USD Billion)
Source: Secondary Research, Expert Interviews, and MAARECO Analysis
IoT Security, or Internet of Things security, refers to the measures and protocols implemented to safeguard the interconnected network of devices and systems within the Internet of Things ecosystem. As the number of connected devices grows, ranging from smart appliances to industrial sensors, IoT Security addresses the vulnerabilities associated with potential cyber threats. It involves implementing encryption, authentication, access controls, and monitoring mechanisms to protect data integrity, confidentiality, and the overall functionality of interconnected devices. Ensuring robust IoT Security is essential to mitigate the risks of unauthorized access, data breaches, and disruptions, fostering a secure and trustworthy IoT environment.
IoT Security Market Drivers
Proliferation of Connected Devices and IoT Adoption
One primary driver for the IoT Security market is the proliferation of connected devices and the widespread adoption of IoT across industries. The number of connected devices is expected to surpass 41 billion by 2025. As organizations integrate IoT devices into critical infrastructure, healthcare systems, and smart homes, the attack surface for cyber threats expands. The growing dependence on interconnected systems heightens the need for robust security measures to protect against potential vulnerabilities and cyber-attacks. The increased prevalence of IoT adoption across sectors, driven by the promise of efficiency and automation, fuels the demand for comprehensive IoT security solutions. Organizations recognize the critical importance of securing these diverse and interconnected devices, creating a significant market driver for innovative and scalable IoT security technologies.
Escalating Cybersecurity Threats Targeting IoT Devices
The escalating frequency and sophistication of cybersecurity threats targeting IoT devices serve as a compelling driver for the IoT Security market. As highlighted by the Cybersecurity & Infrastructure Security Agency (CISA), IoT devices are increasingly becoming targets for various cyber attacks, including ransomware, distributed denial-of-service (DDoS) attacks, and unauthorized access attempts. The Mirai botnet attack, for instance, exploited vulnerable IoT devices to launch massive DDoS attacks. The rising prominence of such threats underscores the urgency for robust security measures tailored to the unique characteristics of IoT ecosystems. The potential consequences of compromised IoT devices, ranging from privacy breaches to disruptions in critical services, intensify the demand for advanced security solutions. This driver compels organizations to invest in IoT security technologies that can effectively detect, prevent, and mitigate a diverse array of cyber threats targeting their interconnected devices and systems.
IoT Security Market Restraints
Lack of Standardization and Interoperability
A significant restraint in the IoT Security market is the lack of standardization and interoperability among diverse IoT devices and platforms. According to the National Institute of Standards and Technology (NIST), the absence of uniform security standards makes it challenging to establish consistent security measures across the vast landscape of IoT devices. Devices from different manufacturers often operate on proprietary protocols, leading to compatibility issues and making it difficult to implement standardized security practices. This lack of uniformity hampers the development and adoption of comprehensive security solutions. Organizations struggle to apply consistent security policies, resulting in fragmented security postures that leave potential vulnerabilities unaddressed. Addressing this restraint requires collaborative efforts within the industry to establish and adhere to common security standards, promoting interoperability and enabling the seamless integration of security measures across diverse IoT ecosystems.
Resource Constraints in IoT Devices
Another significant restraint for the IoT Security market is the resource constraints inherent in many IoT devices. Numerous IoT devices are designed with limited processing power, memory, and energy resources to ensure cost-effectiveness and operational efficiency. According to the Internet Engineering Task Force (IETF), resource-constrained devices may struggle to implement robust security protocols due to these limitations. Strong encryption, complex authentication mechanisms, and continuous monitoring can strain the limited resources of IoT devices, potentially affecting their performance and functionality. This constraint poses a challenge for implementing comprehensive security measures, as stringent security protocols may not be feasible for resource-constrained devices. Overcoming this restraint requires the development of lightweight and efficient security solutions tailored to the specific constraints of IoT devices, ensuring that security measures do not compromise the functionality or operational efficiency of these devices in diverse IoT applications.
IoT Security Market Opportunities
Edge Computing Integration for Enhanced Security
An intriguing opportunity in the IoT Security market involves the integration of edge computing to enhance security measures. According to the National Institute of Standards and Technology (NIST), edge computing, which involves processing data closer to the source of generation, reduces latency and enhances real-time analysis. This proximity can be leveraged to implement security measures directly at the edge, allowing for quicker threat detection and response. The opportunity lies in developing security solutions that utilize edge computing capabilities to analyze and filter data locally, minimizing the need for transmitting sensitive information to centralized servers. This approach not only improves response times but also reduces the attack surface for potential cyber threats. As edge computing gains prominence in IoT deployments, the convergence of edge computing and security presents a strategic opportunity for IoT Security providers to innovate and offer more effective and efficient security solutions tailored to the distributed nature of IoT environments.
Blockchain for Enhanced Data Integrity
An emerging opportunity in the IoT Security market involves the utilization of blockchain technology to enhance data integrity and secure transactions within IoT ecosystems. According to the National Institute of Standards and Technology (NIST), blockchain’s decentralized and tamper-resistant nature makes it well-suited for ensuring the integrity of data exchanged between IoT devices. The opportunity lies in developing security solutions that leverage blockchain to create transparent and immutable ledgers of IoT device interactions and data exchanges. This approach enhances trust among stakeholders, mitigates the risk of data tampering, and provides a secure foundation for IoT transactions. As industries like supply chain and healthcare increasingly rely on IoT for data-driven decision-making, the integration of blockchain offers a strategic opportunity for IoT Security providers to enhance the credibility and reliability of data within IoT networks, contributing to a more secure and trustworthy IoT ecosystem.
IoT Security Market Challenges
Lifecycle Management of IoT Devices
A significant challenge in the IoT Security market is the effective management of the lifecycle of IoT devices, encompassing their deployment, maintenance, and end-of-life considerations. According to the Internet Society, the sheer volume and diversity of IoT devices make it challenging for organizations to implement consistent security measures throughout the entire device lifecycle. The challenge begins with secure device provisioning during deployment, ensuring that devices are configured with strong security credentials. Subsequently, maintaining and updating security measures become crucial to address evolving threats. However, many IoT devices, especially those in constrained environments, lack the necessary mechanisms for seamless and secure updates. The end-of-life phase introduces concerns about decommissioning devices securely to prevent them from becoming entry points for cyber threats. Effectively managing the complete lifecycle of IoT devices requires standardized security practices, collaboration among stakeholders, and industry-wide initiatives to address the unique challenges posed by diverse devices across various sectors.
Inadequate Security by Design Practices
Another critical challenge for the IoT Security market is the widespread lack of security-by-design practices in the development of IoT devices and systems. The National Telecommunications and Information Administration (NTIA) notes that many IoT devices are designed with a primary focus on functionality and cost, often neglecting robust security measures. The challenge lies in the insufficient integration of security considerations into the initial design and development phases of IoT solutions. Inadequate security-by-design practices result in devices with vulnerabilities that can be exploited by malicious actors. As IoT devices become integral to critical infrastructure, homes, and industrial operations, the consequences of security lapses can be severe. Addressing this challenge necessitates a shift in industry practices towards prioritizing security in the early stages of IoT device development. Promoting secure coding practices, incorporating security into device architecture, and fostering awareness among developers about the importance of security by design are essential steps in mitigating the challenges associated with inadequate security practices in the IoT landscape.
Regional Trends
North America: North America, particularly the United States, has been at the forefront of IoT adoption and innovation. The region has a strong focus on IoT security due to its significant presence of IoT deployments across various sectors. The market is driven by stringent data privacy regulations and the increasing number of cyber threats. North America is also home to several leading IoT security solution providers and has a mature ecosystem of cybersecurity companies.
Europe: Europe has witnessed substantial growth in the IoT security market, driven by increasing regulatory compliance requirements. The General Data Protection Regulation (GDPR) and the Network and Information Security (NIS) Directive have compelled organizations to prioritize IoT security measures. European countries have also been proactive in implementing secure IoT frameworks and fostering collaboration between government, industry, and academia.
Asia Pacific: The Asia Pacific region has emerged as a significant market for IoT and IoT security due to its growing industrial and manufacturing sectors, smart city initiatives, and digital transformation efforts. Countries like China, Japan, and South Korea are investing heavily in IoT technologies, which has led to increased demand for IoT security solutions. The region also faces unique challenges, including a diverse regulatory landscape and the need for localized security solutions tailored to specific cultural and market requirements.
Latin America: Latin America is experiencing a steady growth in IoT deployments, primarily driven by smart city projects, agriculture, and energy sectors. As IoT adoption expands, the demand for IoT security solutions is increasing. However, the region faces challenges related to infrastructure limitations, fragmented regulatory environments, and the need for awareness and education about IoT security best practices.
Middle East and Africa: The Middle East and Africa region are witnessing increased IoT adoption in sectors such as transportation, healthcare, and oil and gas. Governments in the region are investing in smart city initiatives and digital transformation, leading to growing demand for IoT security solutions. However, challenges include cybersecurity vulnerabilities, lack of skilled professionals, and the need for stronger regulatory frameworks.
Key Players
Key players operating in the global IoT Security market are Cisco, IBM, Check Point Software Technologies, Intel, Microsoft, AWS, Broadcom, Gemalto, ForgeRock, Mocana, Fortinet, Zingbox, Infineon, CENTRI, Armis, Allot, and SecuriThings.
PRICE
ASK FOR FREE SAMPLE REPORT