Global Identity and Access Management Market, By Component (SSO, Password Management, Advanced Authentication, Directory Services, Provisioning), Deployment Mode, Organization Size, Industry Vertical, and Region – Industry Analysis and Forecast to 2030
The global identity and access management market is expected to grow from USD 17.30 billion in 2023 to USD 37.73 billion by 2030 at a CAGR of 11.8%. The Identity and Access Management (IAM) market is propelled by the escalating need for robust cybersecurity solutions. With increasing cyber threats and data breaches, organizations prioritize IAM to secure digital identities and control access to sensitive information. IAM ensures regulatory compliance, enhances user experience, and mitigates risks, driving its adoption across diverse industries.
Figure 1: Global Identity and Access Management Market Size, 2023-2030 (USD Billion)
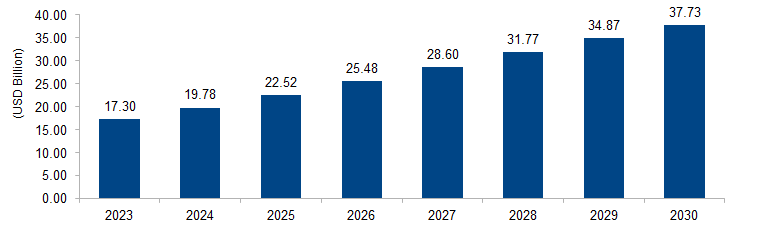
Source: Secondary Research, Expert Interviews, and MAARECO Analysis
Identity and Access Management (IAM) is a comprehensive framework that governs the management of digital identities and regulates access to computer systems, networks, and data. IAM solutions authenticate and authorize individuals, ensuring they have the appropriate level of access based on their roles and responsibilities. By managing user identities and permissions throughout their lifecycle, IAM enhances cybersecurity, safeguarding against unauthorized access and data breaches. This involves processes such as user provisioning, authentication, single sign-on, and access governance. IAM not only strengthens security but also streamlines administration, compliance, and user experience across diverse applications and platforms within an organization’s IT ecosystem.
Identity and Access Management Market Drivers
Rising Cybersecurity Threats and Data Breaches
A major driver propelling the Identity and Access Management (IAM) market is the escalating threat landscape of cybersecurity, characterized by a surge in cyber attacks and data breaches. As cyber threats become more sophisticated, organizations are compelled to fortify their security measures. According to a report by the Federal Bureau of Investigation (FBI), cybercrime costs reached $4.2 billion in the US in 2020. IAM solutions play a pivotal role in mitigating these risks by ensuring that only authorized users have access to sensitive systems and data. The implementation of IAM helps prevent unauthorized access, identity theft, and other cyber threats, making it a critical component of an organization’s cybersecurity strategy. As the frequency and severity of cyber attacks continue to rise, the demand for robust IAM solutions is expected to grow, driven by the imperative to safeguard digital assets and maintain the integrity of sensitive information.
Regulatory Compliance Requirements
The stringent regulatory landscape and compliance requirements governing data protection and privacy represent a significant driver for the Identity and Access Management market. Governments and regulatory bodies worldwide are imposing strict guidelines to protect sensitive information and ensure responsible handling of personal data. For instance, the European Union’s General Data Protection Regulation (GDPR) mandates stringent measures for data protection. Non-compliance with such regulations can result in severe penalties. IAM solutions aid organizations in achieving and maintaining regulatory compliance by managing user access and permissions, tracking user activity, and enforcing security policies. According to a report from the Information Commissioner’s Office (ICO) in the UK, GDPR-related fines exceeded £42 million in 2020. The growing awareness of regulatory risks and the need to avoid legal consequences drive organizations to invest in IAM solutions to ensure adherence to compliance standards, creating a robust and compliant security infrastructure.
Identity and Access Management Market Restraints
Complexity and Integration Challenges
A significant restraint in the Identity and Access Management (IAM) market is the inherent complexity of implementing and integrating IAM solutions within diverse organizational IT ecosystems. According to a study by the National Institute of Standards and Technology (NIST), organizations often face challenges in aligning IAM systems with existing infrastructure, applications, and cloud services. The complexity increases as businesses deploy hybrid or multi-cloud environments, requiring seamless integration across platforms. The intricacies of IAM deployment can lead to extended implementation times, higher costs, and potential disruptions to regular business operations. Overcoming these challenges necessitates strategic planning, standardized IAM protocols, and collaboration between IT teams and IAM solution providers to ensure a smooth integration process that aligns with an organization’s specific needs and technology stack.
User Resistance and Privacy Concerns
Another significant restraint for the IAM market is the resistance from users and concerns about privacy implications. The implementation of IAM often involves changes to user authentication processes, password policies, and access controls, which can be met with resistance from employees. According to a survey by the Electronic Frontier Foundation (EFF), 45% of respondents express concerns about the impact of IAM on user privacy. Users may perceive increased scrutiny and surveillance, leading to apprehension about the collection and management of their personal information. Overcoming user resistance requires effective communication, education on the benefits of IAM in enhancing security, and transparent policies that address privacy concerns. Striking a balance between stringent security measures and user-friendly experiences is crucial for successful IAM implementation, ensuring that security measures are embraced rather than met with resistance from the workforce.
Identity and Access Management Market Opportunities
Biometric Authentication Advancements
An emerging opportunity within the Identity and Access Management (IAM) market is the continued advancement and adoption of biometric authentication technologies. Biometric methods, such as fingerprint recognition, facial recognition, and iris scanning, offer a more secure and convenient alternative to traditional password-based authentication. According to a report from the National Institute of Standards and Technology (NIST), the use of biometrics can significantly enhance security, with false acceptance rates as low as 0.001%. IAM providers can capitalize on this opportunity by integrating and enhancing biometric authentication within their solutions. The adoption of biometrics aligns with the increasing demand for frictionless user experiences while bolstering security measures. As industries explore innovative authentication methods, IAM solutions incorporating advanced biometrics present a strategic opportunity to cater to evolving security needs and provide users with secure and seamless access to digital assets.
Internet of Things (IoT) Integration
The proliferation of Internet of Things (IoT) devices presents a significant opportunity for the IAM market. As the number of connected devices continues to grow, securing access and identities within IoT ecosystems becomes imperative. The global spending on IoT is projected to reach $1.1 trillion by 2023. IAM solutions can play a crucial role in managing and securing identities, authorizing device interactions, and ensuring the integrity of data generated by IoT devices. IAM providers can seize this opportunity by developing specialized solutions that cater to the unique identity and access challenges posed by IoT deployments. By integrating IAM with IoT ecosystems, organizations can establish comprehensive security frameworks that protect both traditional IT assets and the expanding array of IoT devices, fostering a secure and interconnected digital environment.
Identity and Access Management Market Challenges
Shadow IT and Bring Your Own Device (BYOD) Risks
A significant challenge for the Identity and Access Management (IAM) market is the proliferation of Shadow IT and the increasing prevalence of Bring Your Own Device (BYOD) practices within organizations. According to a study by the National Cyber Security Centre (NCSC), employees often utilize unauthorized applications and devices, contributing to the Shadow IT phenomenon. This decentralized approach to IT poses challenges for IAM systems, as they struggle to manage and secure identities across a diverse range of platforms and applications. The use of personal devices in the workplace adds another layer of complexity. IAM solutions must adapt to address the risks associated with unmanaged devices and unsanctioned applications, ensuring that access controls and security measures extend to all endpoints. Overcoming this challenge requires IAM providers to offer solutions that seamlessly integrate with diverse platforms, support BYOD policies, and effectively mitigate the risks associated with Shadow IT practices.
Evolving Cyber Threats and Social Engineering
The ever-evolving nature of cyber threats, coupled with sophisticated social engineering tactics, presents a formidable challenge for the IAM market. According to a report from the Federal Bureau of Investigation (FBI), cybercriminals continue to refine their strategies, often relying on social engineering to exploit human vulnerabilities. Phishing attacks, in which attackers manipulate individuals into divulging sensitive information, remain a prevalent threat. IAM systems need to go beyond traditional authentication methods to safeguard against such threats. The challenge lies in designing IAM solutions that can detect and mitigate the risks associated with social engineering, ensuring that even if credentials are compromised, additional layers of security are in place to prevent unauthorized access. As cyber threats continue to evolve, IAM providers must stay ahead of the curve, incorporating advanced threat detection and adaptive security measures to protect against the increasingly sophisticated tactics employed by malicious actors.
Key Players
Key players operating in the global identity and access management market are CA Technologies, IBM, Oracle, Microsoft, Ping Identity, Okta, Micro Focus, Centrify, Hitachi ID Systems, Evidian, SailPoint, SecureAuth, Exostar, Optimal IdM, OpenText, Idaptive, OneLogin, One Identity, Zoho Corp, and Core Security.
PRICE
ASK FOR FREE SAMPLE REPORT